While Telegram offers strong encryption, vulnerabilities in user devices and phishing attacks can lead to potential hacking.
Understanding Telegram Security
Encryption Methods
Telegram employs a unique encryption protocol known as MTProto. It offers two types of chats: Cloud Chats and Secret Chats. Cloud Chats use server-client encryption, where messages are encrypted on the sender’s device and decrypted on the recipient’s device. Secret Chats utilize end-to-end encryption, ensuring that only the sender and recipient can read the messages. This method is similar to the encryption used by WhatsApp, which relies on the Signal Protocol, renowned for its high security.
Privacy Policies
Telegram’s privacy policy emphasizes user data protection and minimal data retention. The policy states that only the phone number, contacts, and basic account info are stored. Telegram claims to store less information compared to other messaging apps like Facebook Messenger or Skype. The company asserts that it does not share user data with third parties and only discloses information if legally compelled, which is a rare occurrence.
User Authentication
User authentication on Telegram is primarily based on mobile phone numbers. When registering or logging in, users receive a one-time SMS verification code. Telegram offers Two-Step Verification (2SV), where users can set up an additional password. This feature significantly enhances security, making it more difficult for unauthorized users to access an account, even if they have access to the phone number. Telegram’s approach to authentication is straightforward yet effective, similar to methods used by other major platforms like Google and Apple.
Common Vulnerabilities in Messaging Apps
Software Flaws
Software flaws in messaging apps often stem from coding errors or outdated software components. These vulnerabilities can lead to various issues, such as data breaches or unauthorized access. A well-known bug in an older version of WhatsApp allowed hackers to inject spyware through voice calls, even if the call wasn’t answered.
Key Comparisons of Software Flaws in Popular Messaging Apps:
| Messaging App | Type of Flaw | Impact | Resolution Time |
|---|---|---|---|
| Spyware Injection via Voice Call | Access to personal data | Patched within weeks | |
| Signal | Attachment Handling Bug | Potential Data Exposure | Fixed promptly |
| Telegram | Decryption Key Leak in Cloud Chats | Data Vulnerability | Continuously updated for security |
Note: The resolution time and impact are based on reported incidents and may vary for different cases.
End-Point Security Risks
End-point security risks in messaging apps arise when the user’s device is compromised. Regardless of the app’s encryption strength, if the end device (like a smartphone or computer) is infected with malware, messages can be intercepted or manipulated.
Comparison of End-Point Security Measures:
| Messaging App | End-Point Security Feature | Effectiveness | User Responsibility |
|---|---|---|---|
| End-to-End Encryption | High, if device is secure | Keep device malware-free | |
| Telegram | Secret Chats with Self-Destruct | High, with user engagement | Active engagement in security settings |
| Signal | Screen Security to Block Screenshots | Adds an extra layer | Regular updates and device security |
Note: The effectiveness of these features largely depends on the user’s awareness and proactive measures to secure their devices.
Case Studies: Telegram Hacking Incidents
Documented Breaches
One significant breach in Telegram’s history occurred in 2016, when Iranian hackers reportedly compromised more than a dozen accounts and identified phone numbers of 15 million Iranian users. This breach was notable due to Telegram’s popularity in Iran, where it had about 20 million users at the time. The attack exploited a weakness in the SMS text message-based login process. Although the core encryption of Telegram was not broken, the incident highlighted the vulnerability of relying on SMS for authentication.
Another incident involved activists in Hong Kong in 2019, where Telegram acknowledged that it suffered a powerful cyberattack that coincided with protests. The attackers used a Distributed Denial of Service (DDoS) attack, overwhelming the system with a flood of requests. While message content remained secure, the service disruption raised concerns about targeted attacks against secure messaging platforms.
Methods Used by Hackers
Hackers often employ a variety of methods to compromise messaging apps like Telegram. One common method is phishing, where users are tricked into giving away access codes or sensitive information. In the case of the 2016 incident in Iran, hackers used SMS interception to gain access to user accounts.
Another method is exploiting software vulnerabilities. Though Telegram prides itself on encryption, vulnerabilities in app interfaces or operating systems can provide hackers with loopholes. For instance, hackers can exploit outdated software on a user’s device to gain unauthorized access to their messages.
State-sponsored attacks use sophisticated methods, such as deploying malware that targets specific users to intercept messages before they are encrypted. The DDoS attack against Telegram in Hong Kong is an example of how external forces can attempt to disrupt secure communication platforms.
The security of Telegram hinges not just on its encryption technology but also on external factors like the security of the user’s device and the reliability of verification methods like SMS. The evolving nature of cyber threats means that messaging apps must continuously update and strengthen their security measures to protect user data.
Protective Measures for Users
Secure Chat Settings
Telegram’s Secret Chats offer a robust level of security for users. These chats are not only end-to-end encrypted, but also they’re not stored on Telegram’s servers. This ensures that conversations remain confidential between the sender and recipient. Self-destruct timers in Secret Chats allow messages to disappear after a set time, leaving no trace on either device.
Another critical setting is disabling cloud backups for sensitive chats. While convenient, backups stored on cloud servers can become potential vulnerabilities. Users concerned with maximum privacy should consider this trade-off.
Account Security Practices
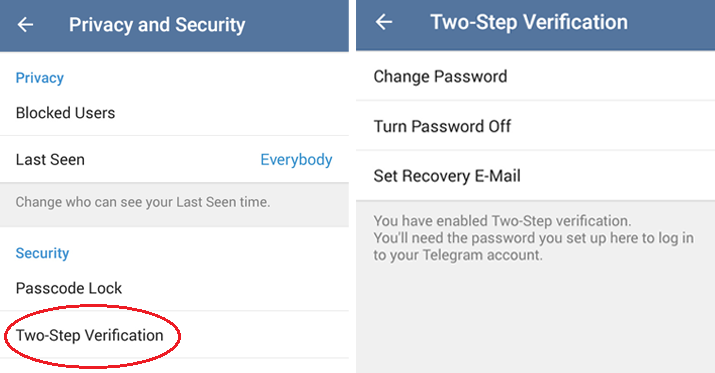
Activating Two-Step Verification (2SV) is a cornerstone of account security on Telegram. This feature, which adds a password in addition to the SMS code, significantly increases account security. It’s a simple yet effective barrier against unauthorized access.
Being vigilant against phishing attacks is crucial. Users should be wary of unsolicited messages or emails that ask for personal information or direct them to suspicious websites. Telegram will never ask users for their passwords or verification codes outside of the login process.
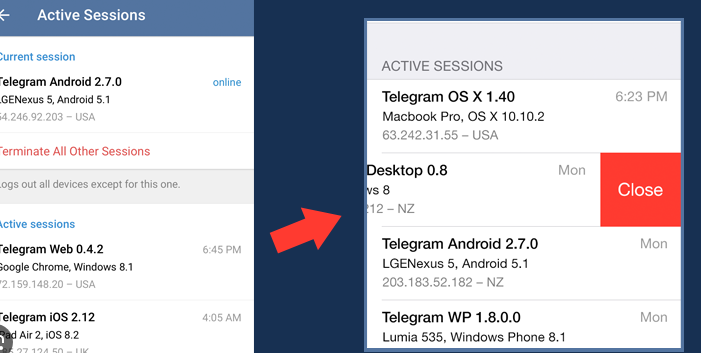
Regularly reviewing active sessions in the Telegram app can prevent unauthorized access. This feature shows all devices where the user’s account is logged in, and allows them to terminate any session that appears suspicious.
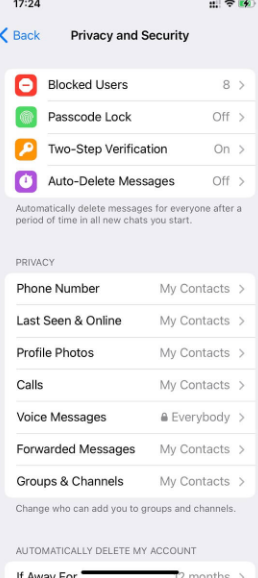
For additional security, users can enable a Passcode Lock for the Telegram app. This feature requires a code to access the app, thus providing another layer of protection in case the user’s device is lost or stolen.
The Role of Government and Surveillance
Legal Access to Data
Governments around the world have various laws and regulations that can compel messaging services like Telegram to provide access to user data. The United States, for example, has the Patriot Act and Electronic Communications Privacy Act (ECPA), which allow certain government agencies to request access to electronic communications for national security or law enforcement purposes. Similarly, the European Union’s GDPR has clauses for legal data access, though it is primarily focused on data protection and privacy.
Russia and China have more direct control over internet communications. They have laws requiring companies to store data on local servers and provide government access when demanded. Telegram’s refusal to comply with such demands in Russia led to its temporary ban in the country.
Note that Telegram’s end-to-end encryption in Secret Chats makes it technically challenging for governments to access message content. However, metadata like user contacts and times of messaging can still be subject to legal requests.
Global Surveillance Concerns
Global surveillance initiatives, like the Five Eyes alliance (involving the USA, UK, Canada, Australia, and New Zealand), raise concerns about the extent of government monitoring over digital communications. These alliances can lead to increased cooperation between countries in sharing digital intelligence, potentially bypassing national privacy protections.
Surveillance laws vary significantly across countries. While some nations have strict privacy laws, others grant their governments wide-ranging surveillance powers. This disparity leads to a complex global landscape where the privacy of a message can depend heavily on the jurisdiction it passes through.
The use of mass surveillance technologies by governments to monitor communications without specific warrants is a growing concern. This technology can potentially infringe on individual privacy rights and has led to debates about the balance between national security and personal privacy.
The role of government and surveillance in the context of messaging apps like Telegram is a complex issue, balancing legal data access requirements and global surveillance concerns against individual privacy rights. The legal landscape is ever-evolving, reflecting the ongoing debate between security and privacy in the digital age.